VENDILIGENCE™
Point-in-Time Cybersecurity Assessment
Our Point-in-Time Cybersecurity Assessment (CSA) evaluates the most critical elements of your vendor's or supplier's cybersecurity readiness, helping you make informed risk-based decisions. We review their cybersecurity policies and responses, providing both overall and individual risk ratings on areas like security testing, information security governance, and sensitive data security.

PRODUCT TOUR
See it in Action: Take a tour of the Point-in-Time Cybersecurity Assessment
Outsourcing this crucial review to Venminder means obtaining a clear picture of your vendor's or supplier's cybersecurity readiness level, helping you to identify areas of strength and weakness, ensuring secure and robust relationships.
Most Commonly Used For:
Technology Suppliers, Data-Handling Vendors, and SaaS Providers
Venminder is trusted by over 1,200 companies worldwide






















Cybersecurity assessments to pinpoint areas where vendors
may be exposing your organization to cyber threats
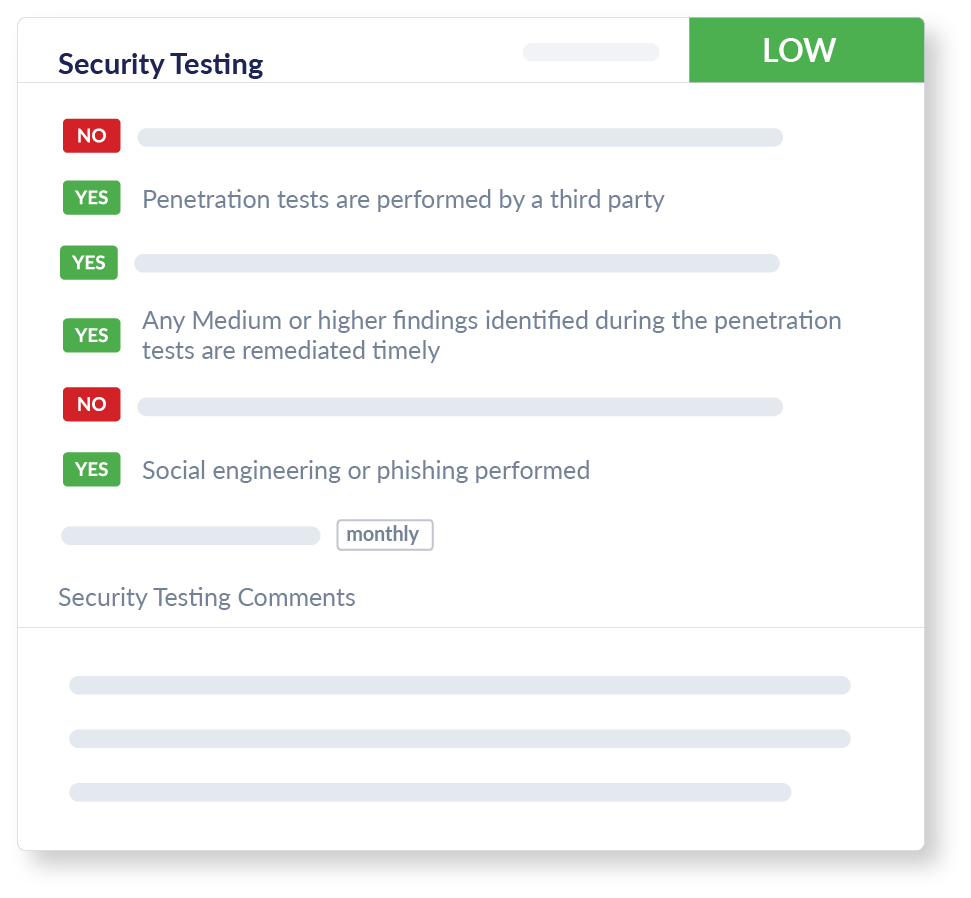
Security Testing
We review your vendor or supplier’s Security Testing protocols, including insights into internal and third-party penetration testing, looking closely at the date, scope, and frequency. We evaluate their vulnerability scans and social engineering tests. We aim to provide you with insights into important data and key areas of security testing to help ensure your vendor or supplier is safeguarding against cyber threats.
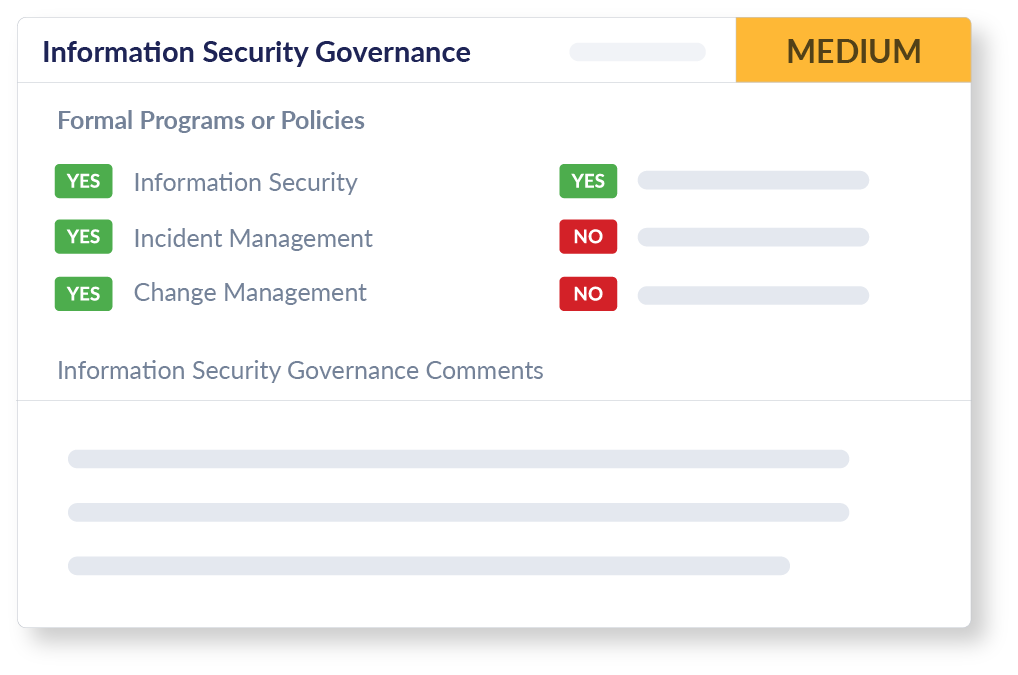
Information Security Governance
Our assessment looks at whether your vendors or supplier’s have documented and current formal programs, policies, and practices. We look at if there are plans for Information Security, Incident Management, and Change Management. We also review represented practices like employee and contractor security training. Our review ensures you are aware of their preparedness to handle cybersecurity incidents and maintain your data's integrity.
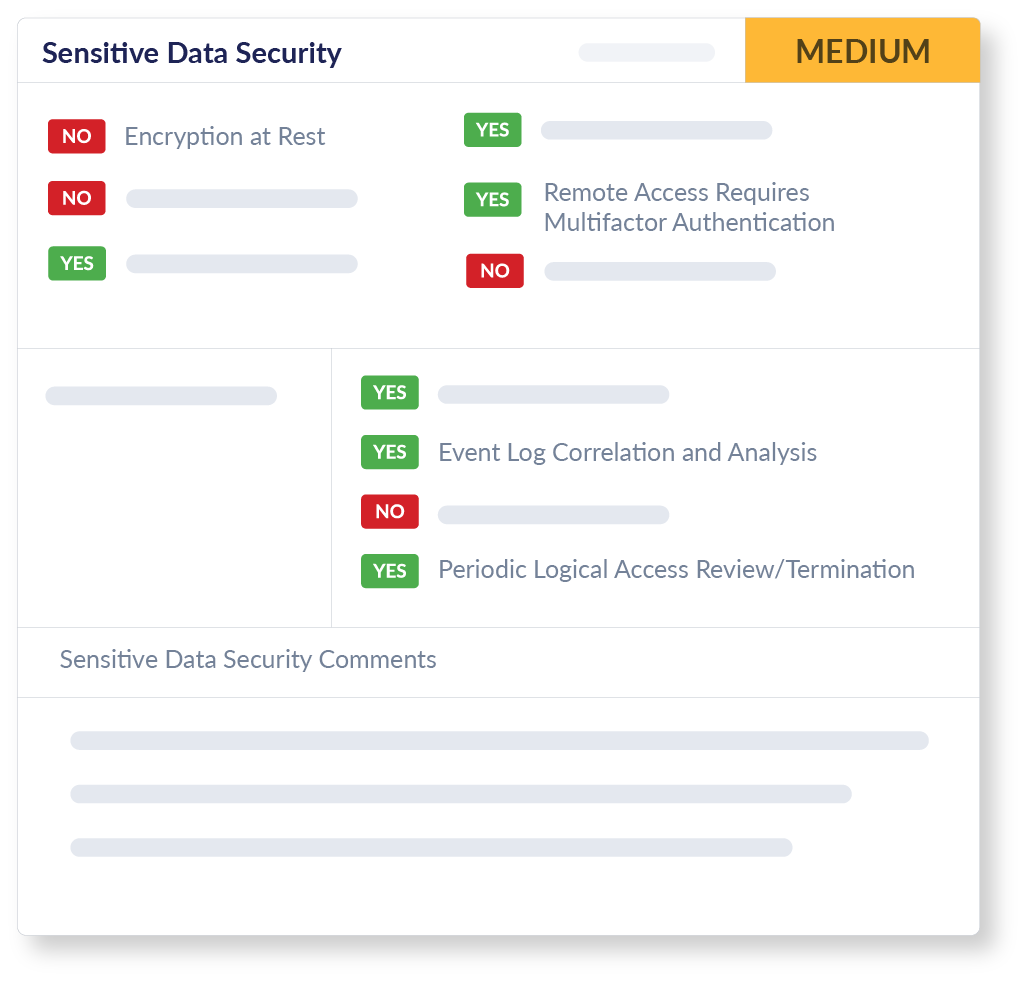
Sensitive Data Security
We undertake a detailed evaluation of your vendor or supplier's Sensitive Data Security measures. This covers encryption methods both in transit and at rest, secure device baselining, and logical access management. Additionally, our assessment delves into their incident detection and response capabilities. Our focus is to provide you with the most important details on how they protect sensitive data so you can make better risk-based decisions.
Gain a valuable lens into the overall robustness and resilience of your vendor's or supplier’s technological infrastructure and processes
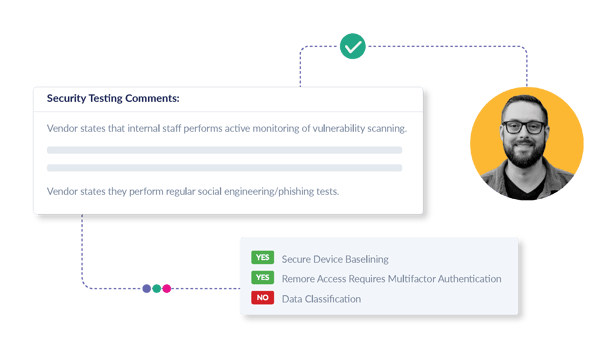
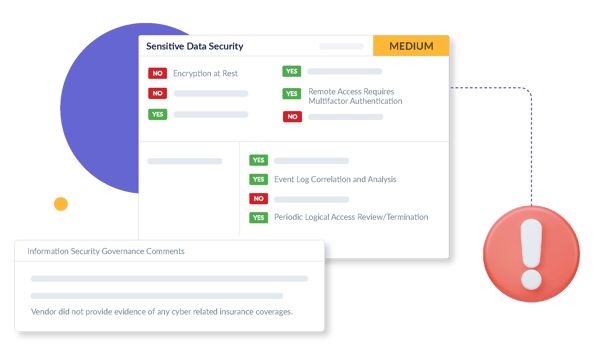
Key Cybersecurity Elements Are Risk-Rated
Our CSA dives into core aspects of cybersecurity, spanning Security Testing, Sensitive Data Security, comprehensive Employee and Vendor Management protocols, and proactive Incident Response practices.
Stay Ahead with a Proactive Defense
Proactively identify and address potential vulnerabilities, substantially reducing the risk of breaches and the associated regulatory and financial repercussions.
Improve vendor and supplier oversight by identifying gaps or weaknesses
Understanding your vendor's or supplier’s cybersecurity posture is critical. Without it, those third parties could become your organization's most vulnerable point for cyber breaches. A single lapse in their defense mechanisms can expose sensitive data, disrupt operations, and erode trust with both partners and customers.
With Venminder's Point-in-Time Cybersecurity Assessment, every document and response from your vendor or supplier undergoes meticulous analysis by our experienced and certified professionals, providing depth, precision, and a level of expertise that grants you solid confidence in the results.


Ensure your vendors and suppliers are aligned with cybersecurity standards
Cybersecurity is a focal point for regulators. Failing to demonstrate proactive measures could result in hefty fines, loss of customer trust, and severe reputational damage. Regulatory bodies are intensifying their focus on third-party vendor and supplier relationships, ensuring that organizations not only protect their internal systems but also extend security protocols across their entire supply chain.
Venminder reviews multiple aspects of your vendor's or supplier’s cybersecurity stance. We check whether security testing is performed and how they are safeguarding sensitive data. We also evaluate employee training protocols and assess their incident response readiness. This review is meticulously mapped to key industry frameworks, regulations, and laws, ensuring your vendor or supplier meets cybersecurity regulatory expectations.
Create a risk-based framework for assessing vendor and supplier cybersecurity readiness
Keeping up with reviewing your vendors’ or suppliers’ most current cybersecurity measures can be time-consuming and challenging, especially for organizations with a large volume of third-party vendors and suppliers. Without a structured process or system to capture and log due diligence documents and data, it can easily lead to potential oversights.
Our assessment offers a standardized and reliable way to compare and evaluate your vendor's or supplier's cybersecurity readiness. You gain an understanding into the adequacy of their cybersecurity measures, with easy to understand risk-based ratings that you can use to identify action items and priorities for follow-up due diligence.

How it works
STEP 1
Alleviate the burden of chasing for evidence and documents
Venminder’s team directly works with your vendor or supplier to collect the numerous technical documents needed for a qualified and comprehensive assessment of cybersecurity readiness.
STEP 2
Cybersecurity measures assessed by professionals
Venminder’s experienced information security professionals thoroughly review the evidence to assess whether your vendor or supplier has implemented the most critical elements for cybersecurity readiness.

STEP 3
Streamlined Cybersecurity Evaluations
You receive an easy-to-understand risk assessment on your vendor or supplier's data protection controls that is available on the Venminder platform and as a downloadable PDF, our reports are easy to understand and are perfect for internal sharing, review, and decision-making.
STEP 4
Improve risk-based decisions with the right insights
You and your organization’s decision-makers can now make an informed choice about any risks presented by the vendor or supplier and whether you need to take action in addressing areas of cybersecurity weakness.

Discover why Venminder
is top-rated by customers
Know if vendors and suppliers are in compliance with
industry guidelines, frameworks, standards and laws
Technology Standards and Frameworks
AICPA Trust Services Criteria
ISO/IEC 27001:2022
NIST Framework for Improving Critical Infrastructure Cybersecurity version 1.1
NIST SP 800-53 Rev. 5 Security and Privacy Controls for Information Systems and Organizations
NIST SP 800-63b Digital Identity Guidelines
Regulations, Statutes, and Laws
California Consumer Privacy Act
California Privacy Rights Act
Canadian Personal Information Protection and Electronic Documents Act
China Personal Information Protection Law
Colorado Privacy Act
Connecticut Data Privacy Act
EU General Data Protection Regulation
Health Insurance Portability and Accountability Act
Interagency Guidelines Establishing Information Security Standards
Interagency Guidance on Third-Party Relationships
New York Department of Financial Services - 23 NYCRR 500
Industry Guidance
Center for Internet Security – Critical Security Controls v8
FFIEC IT Examination Handbook – Audit Booklet
FFIEC IT Examination Handbook – Business Continuity Booklet
FFIEC IT Examination Handbook – Management Booklet
FFIEC IT Examination Handbook – Operations Booklet
FFIEC IT Examination Handbook – Outsourcing Technology Services
FFIEC IT Examination Handbook - Wholesale Payment Systems Booklet
FINRA Report on Cybersecurity Practices
OCC 2021-36 Authentication and Access to Financial Institution Services and Systems
SEC Regulation SCI reference to NIST 800-53 Rev. 4
Learn about the regulations, standards, guidelines, and laws, that our Point-in-Time Cybersecurity Assessment maps to here >
You won't just hear it from us





Free Sample
Point-in-Time Cybersecurity Assessment
Get a downloadable sample of this cybersecurity readiness risk-based assessment to see exactly how Venminder can help you identify areas at your vendor or supplier requiring attention.
Free Resources
Ensure Your Third Parties are Cybersecurity Ready Before They Handle Your Data

Continuous Monitoring

Software Platform

Why Choose Venminder

Continue your Education





.gif?width=1920&name=Sample-Graphic-Animation%20(1).gif)